Project post originally published on the Crossplane blog
The Crossplane project has spent the last couple months partnering with Ada Logics, an independent third party security research firm, as well as the CNCF and the OSTIF, to perform a security audit of the project. We are excited to announce today that the security audit is officially complete and the full report and findings are available for the public in the Crossplane repository. Completing this thorough audit was a major step to mature, harden, and grow enterprise confidence in the project as we continue on a path towards full graduated status with the CNCF.
Audit Results Summary
Let’s dive into a high-level summary and statistics of the key findings and outcomes of the audit:
- A total of 16 security issues were identified and reported by the Ada Logics team
- 7 issues were deemed Low severity, 8 Medium, and 1 was considered High severity
- 9 issues were found in stable or beta level features of Crossplane and 7 were found in in alpha level features
- 15 of the 16 issues have already been fixed and included in the v1.13 release and patch releases have been published for all currently supported versions of Crossplane
- 2 issues were impactful enough to warrant CVEs being assigned
We are truly grateful to the Ada Logics teams for their rigorous investigation into the Crossplane code base and for responsibly disclosing issues they uncovered to the maintainer team. There is no doubt that this effort has resulted in a hardened and more secure Crossplane deployment that will greatly benefit the entire community.
Threat Model and Scope
The main focus areas of the audit were in the Core Crossplane and Crossplane Runtime repositories. These two repositories contain the critical core functionality and machinery of Crossplane itself, as well as core functionality for a large portion of the Crossplane provider ecosystem, so their importance cannot be understated.
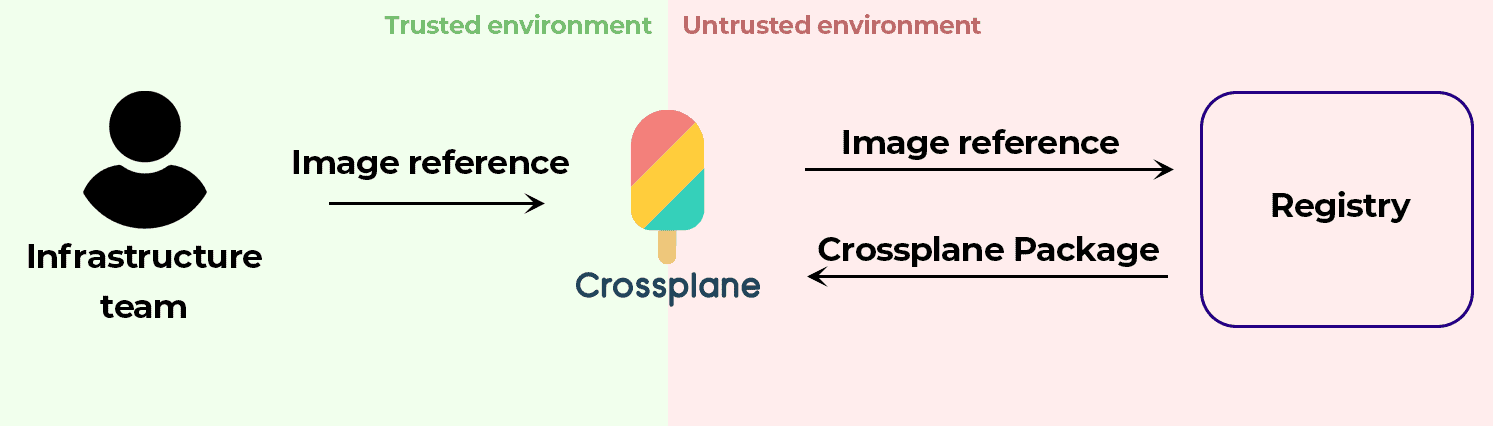
While the entire code base for Crossplane and its runtime were investigated, the audit organically took a strong focus on potential vectors for supply chain attacks. Crossplane provides an opinionated package manager to facilitate the extension of the control plane with new functionality in providers and configurations, for example, to teach Crossplane how to provision resources in AWS. The package manager downloads user defined OCI images, unpacks them, and installs their contents into the control plane. This vector definitely has potential for threat actors to interfere with supply chain attacks in the hopes of achieving malicious outcomes, therefore focusing heavily in this area was deemed critical in the audit.
Another area of strong focus was on the “claim” model that Crossplane provides to developers to provision infrastructure resources through abstractions defined by their platform engineering team. This model exhibits a strong separation of concerns and access permissions between the developers and platform engineers. While platform engineers typically have full access to all of the organization’s infrastructure resources, developers are intentionally given much more limited access to simplified abstractions and APIs that represent the resources they require for their applications. The Ada Logics team focused on this claim model and implementation code to ensure there were no available vectors for escalation of privileges or unauthorized access to resources that were not explicitly intended by the platform team.
High Severity Issue Breakdown
As previously stated, 1 of the 16 security issues identified was deemed to be High severity. Due to this severity and potential for exploit, CVE-2023-38495 has been assigned for this issue. Let’s break down the root cause and remediation for this issue.
When the Crossplane package manager is extending the control plane with user-requested functionality, such as a new provider, it will download the OCI-compliant image from a registry then unpack the resources it contains and apply them to the cluster. While there are mechanisms in place to ensure the package manager is connecting to and downloading from the registry it intends to, there was no further validation to confirm that the actual downloaded content matches what was expected. This is a critical supply chain attack vector, where if a registry had been compromised by a threat actor, they could tamper with the contents of a Crossplane package within that registry and Crossplane would unknowingly download and install the contents of the unsafe package.
This high-severity supply chain attack issue was discussed and resolved with PR #4370. The fix to mitigate this vector was essentially to perform a full verification of the downloaded image and its layers to ensure that the downloaded bytes exactly match their content hashes. This comes with a slight performance penalty during package installation to perform this validation but is well worth the cost due to the security benefits it brings.
Keeping the Security Bar High
The Crossplane project now has both a fuzzing audit and a full security audit completed, and a rigorous security disclosure process has been defined. With all of this security-related work completed, the project now has an excellent security posture defined and we intend to only build on this great foundation.
We invite you to read the detailed report from the audit and we humbly ask the community of users and security professionals to responsibly disclose any vulnerabilities that may be found within the project going forward. Together, we can keep the project secure and safe for all of its adopters!
Crossplane is a community-driven project and we welcome you to join the community and contribute through a variety of opportunities, such as opening and commenting on issues, joining the community meetings, sharing your adoption story, and providing feedback on design docs and pull requests.
We love to hear from the community, as they are exactly what makes this project great.
Whether you are a developer, user, or just interested in what we’re up to, feel free to join us via one of the following methods: